Interview: Hubble Integration Added to DigitalOcean Kubernetes
Exclusive Interview with DigitalOcean on Integrating Hubble into their Kubernetes Offering
Exclusive Interview with DigitalOcean on Integrating Hubble into their Kubernetes Offering
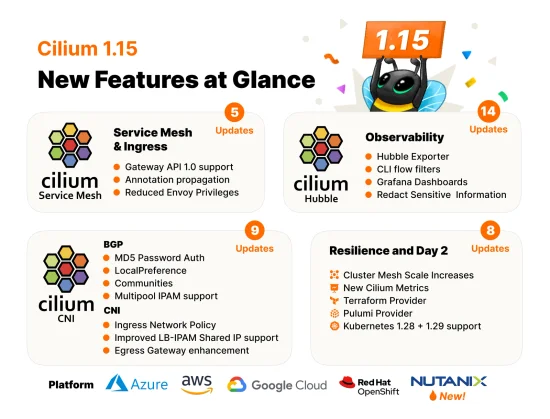
Cilium 1.15 has arrived with Gateway API 1.0 Support, Cluster Mesh Scale Increase, Security Optimizations, and more
There is an amazing lineup of Cilium activities at KubeCon + CloudNativeCon
Welcome to the Cilium User Survey 2021! We are looking to improve Cilium further and are interested in feedback and guidance from our users. Cilium has been a community-driven project from the beginning and the majority of our roadmap has and will continue to be defined by our users. Tell us what you want. Tell us what you are struggling with. Tell us what we can do better.
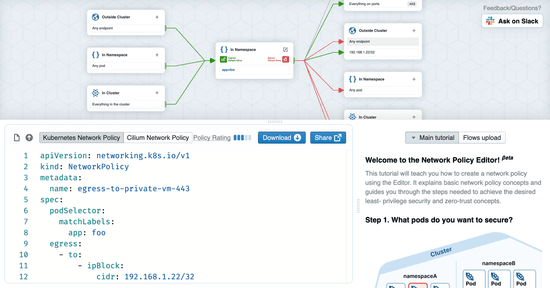
Implementing Network Policy is a critical part of building a secure Kubernetes-based platform, but the learning curve from simple examples to more complex real-world policies is steep. Not only can it be painful to get the YAML syntax and formatting just right, but more importantly, there are many subtleties in the behavior of the network policy specification (e.g. default allow/deny, namespacing, wildcarding, rules combination, etc.). Even an experienced Kubernetes YAML-wrangler can still easily tie their brain in knots working through an advanced network policy use case.
Thomas talks about challenges of security and networking in Linux and Kubernetes and how to build a business on open source technology
Dan and Thomas join the show today to talk about why Cilium is a great choice for organizations looking to build cloud native applications
This is a guest blog by Howard Hao. Howard is working as a Kubernetes infrastructure SRE for Ect888.com. In this guest post, Howard will share how Ect888 uses Cilium & F5 to build a scalable load-balancing infrastructure with BGP for Ect888's production environment.
Thomas joins the Kubernetes Podcast from Google to talk about Cilium
You've probably heard about the new Man in the Middle (MITM) vulnerability in Kubernetes. If you're unfamiliar, a MITM vulnerability works by redirecting a victim's legitimate network traffic through a secret attacker on the network, where the attacker can eavesdrop or actively tamper with the victim's data before sending it to its intended destination. There have been several MITM vulnerabilities in Kubernetes, most of which take advantage of the default overly-permissive CAP_NET_RAW permissions in Kubernetes. However this vulnerability is unique in two ways:1. MITM attacks generally make use of common types of network vulnerabilities, whereas this vulnerability affects the API layer of Kubernetes itself. 2. Unlike most vulnerabilities that are assigned a Common Vulnerabilities and Exposures (CVE), there's no patch or hotfix you can deploy to protect your environment. This vulnerability is also unique in another way:if you're running Cilium without kube-proxy, you aren't vulnerable to it at all. Let's talk about how.
Dan Wendlandt talks about the evolution of cloud networking, eBPF and Cilium for programmable infrastructure
We are excited to announce the Cilium 1.9 release. A total of 2816 commits have been contributed by a community of 251 developers, many of whom made their first contributions this cycle. Cilium 1.9 brings with it several brand new features
For live conversation and quick questions, join the Cilium Slack workspace. Don’t forget to say hi!
Join slack workspace