Interview: Hubble Integration Added to DigitalOcean Kubernetes
Exclusive Interview with DigitalOcean on Integrating Hubble into their Kubernetes Offering
Exclusive Interview with DigitalOcean on Integrating Hubble into their Kubernetes Offering
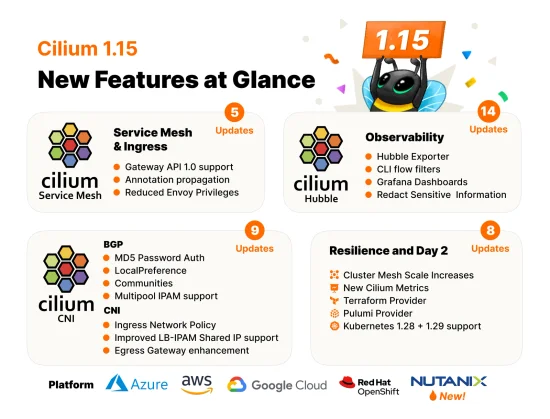
Cilium 1.15 has arrived with Gateway API 1.0 Support, Cluster Mesh Scale Increase, Security Optimizations, and more
There is an amazing lineup of Cilium activities at KubeCon + CloudNativeCon
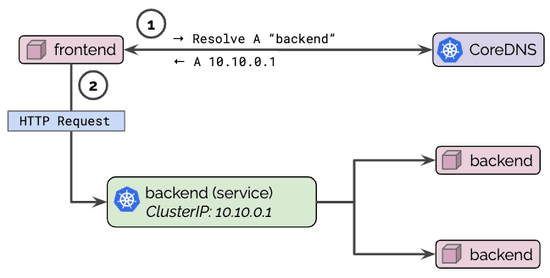
DNS is a common cause for outages and incidents in Kubernetes clusters. For real-world stories, swing by Kubernetes Failure Stories. How do you debug and troubleshoot DNS issues? How do you know a problem is related to DNS? This guide provides a step by step tutorial on how to systematically troubleshoot DNS issues in Kubernetes clusters. We will be using [Hubble] to identify and inspect DNS issues as well as set up monitoring so we can locate DNS issues early on to react even before incidents occur.
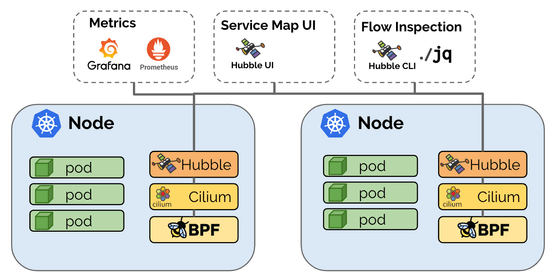
Hubble is a fully distributed networking and security observability platform for cloud native workloads. Hubble is open source software and built on top of Cilium and eBPF to enable deep visibility into the communication and behavior of services as well as the networking infrastructure in a completely transparent manner.

Thomas Graf discusses the recent 1.6 release, some of the security questions/concerns around eBPF, and the future roadmap for the project
The Linux Plumbers Conference 2019 is coming up September 9-11 in Lisbon, Portugal. There are several tracks featuring eBPF related topics
We are excited to announce the Cilium 1.6 release. A total of 1408 commits have been contributed by the community with many developers contributing for the first time. Cilium 1.6 introduces several exciting new features
On May 25 2019, a security relevant bug has been reported to us via the documented security disclosure channel. It was soon identified that multiple vendors are affected by this vulnerability. This lead to an embargo period which is being lifted today. The bug allows, under certain circumstances, to bypass network security policies. See below for details on the vulnerability and the mitigation.
As with everything we do, we are fully transparent. As it becomes obvious that a simple resolution in this matter is not possible, we follow open source best practices and choose a public forum for the sake of transparency. It was brought to our attention that some of the new eBPF code committed to the Calico repository is violating the license of source code in the Cilium repository.
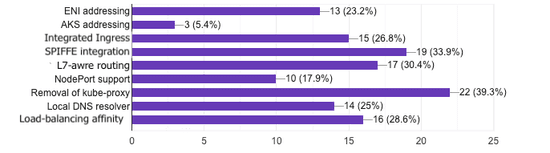
Back in March we have asked our users to provide feedback via our first ever user survey. Many of you have responded and the results are in!
We are excited to announce the Cilium 1.5 release. Cilium 1.5 is the first release where we primarily focused on scalability with respect to number of nodes, pods and services. Our goal was to scale to 5k nodes, 20k pods and 10k services. We went well past that goal with the 1.5 release and are now officially supporting 5k nodes, 100k pods and 20k services. Along the way, we learned a lot, some expected, some unexpected, this blog post will dive into what we learned and how we improved.
For live conversation and quick questions, join the Cilium Slack workspace. Don’t forget to say hi!
Join slack workspace